- Note: The Pre-Shared Keys have been shortened in the Examples to improve readability. The secrets files need to be copied to all IPSec nodes. It is to note that the Pre-Shared key is not a text string as such and care should be taken when key is copied to other systems as these might change the key and make it invalid.
- Mar 17, 2017 Mar 17, 2017 at 16:29 UTC. Brand Representative for Sophos. This info can be found with WebAmind access Support Printable Configuration find in the XML Ipsec Remote Gateway Peer Authentication Config then click on the object for preshared key. Hope this helps.
- Apr 03, 2020 Generating a strong pre-shared key A pre-shared key (also called a shared secret or PSK) is used to authenticate the Cloud VPN tunnel to your peer VPN gateway. As a security best practice, it's recommended that you generate a strong 32-character shared secret.
- Site to Site with Pre-shared Key. Required tasks: Prepare both nodes (see: How to Prepare a Nodegrid Node for IPSec); 2. On one of the nodes create a Pre-Shared Key (see: How to create Pre-shared Keys for IPSec); Create connection configuration file in /etc/ipsec/ipsec.d/ directory as root user.
Contents
With pre-shared keys, the same pre-shared key is configured on each IPSec peer. IKE peers authenticate each other by computing and sending a keyed hash of data that includes the pre-shared key. If the receiving peer is able to independently create the same hash using its pre-shared key, then it knows that both peers must share the same secret. IPSEC preshared key recovery. There is a section on the VPN profile where you can “Print Instructions” - the PSK is included in those instructions. Just confirmed as expected in 5.6.5. For now make sure you disable the pre-warning message before upgrading (and do not re-enable it after upgrading as that breaks it too). IPsec VPNs part four: How to generate and exchange pre-shared keys. Below is a pre-shared key configuration example between two routers. The local router sends it hostname, and the remote.
Introduction
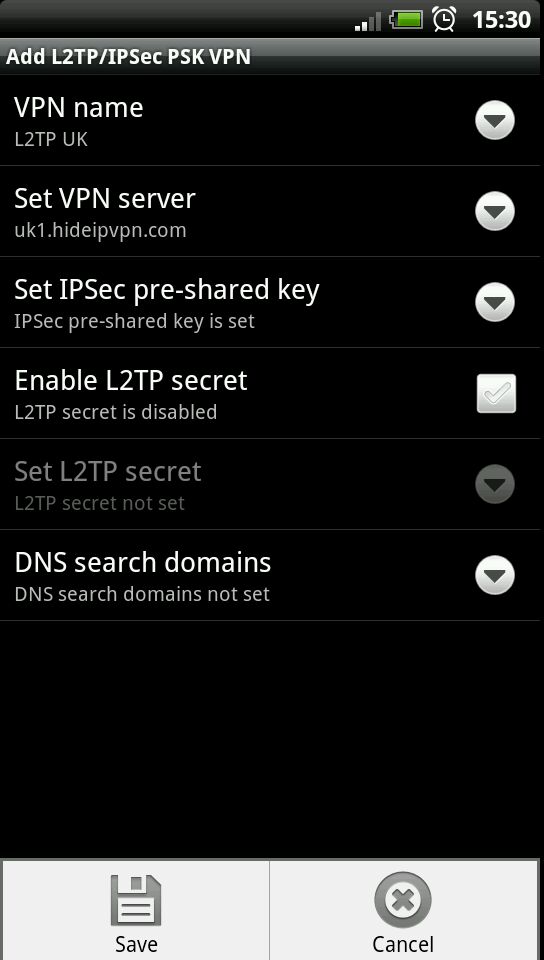
Ipsec Pre Shared Key Psk Generator Free
Cisco IOS® Software Release 12.3(2)T code introduces the functionality that allows the router to encrypt the ISAKMP pre-shared key in secure type 6 format in nonvolatile RAM (NVRAM). The pre-shared key to be encrypted can be configured either as standard, under an ISAKMP key ring, in aggressive mode, or as the group password under an EzVPN server or client setup. This sample configuration details how to set up encryption of both existing and new pre-shared keys.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on this software version:
Cisco IOS Software Release 12.3(2)T
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Configure
This section presents you with the information you can use to configure the features this document describes.
Note: Battlefield 1942 road to rome cd key generator. Use the Command Lookup Tool (registered customers only) to obtain more information on the commands used in this section.
These two new commands are introduced in order to enable pre-shared key encryption:
key config-key password-encryption [master key]
password encryption aes

Ipsec Pre Shared Key Psk Generators
The [master key] is the password/key used to encrypt all other keys in the router configuration with the use of an Advance Encryption Standard (AES) symmetric cipher. The master key is not stored in the router configuration and cannot be seen or obtained in any way while connected to the router.
Once configured, the master key is used to encrypt any existing or new keys in the router configuration. If the [master key] is not specified on the command line, the router prompts the user to enter the key and to re-enter it for verification. If a key already exists, the user is prompted to enter the old key first. Keys are not encrypted until you issue the password encryption aes command.
The master key can be changed (although this should not be necessary unless the key has become compromised in some way) by issuing the key config-key.. command again with the new [master-key]. Any existing encrypted keys in the router configuration are re-encrypted with the new key.
You can delete the master key when you issue the no key config-key... However, this renders all currently configured keys in the router configuration useless (a warning message displays that details this and confirms the master key deletion). Since the master key no longer exists, the type 6 passwords cannot be unencrypted and used by the router.
Note: For security reasons, neither the removal of the master key, nor the removal of the password encryption aes command unencrypts the passwords in the router configuration. Once passwords are encrypted, they are not unencrypted. Existing encrypted keys in the configuration are still able to be unencrypted provided the master key is not removed.
Additionally, in order to see debug-type messages of password encryption functions, use the password logging command in configuration mode.
Configurations
This document uses these configurations on the router:
| Encrypt the Existing Pre-shared Key |
|---|
| Add a New Master Key Interactively |
|---|
| Modify the Existing Master Key Interactively |
|---|
| Delete the Master Key |
|---|
Verify
Linksys Pre Shared Key
There is currently no verification procedure available for this configuration.
Troubleshoot
Pre Shared Key For Wlan
There is currently no specific troubleshooting information available for this configuration.